Defending Against a 1.2Tbps DDoS Attack: A Case Study with Interserver

At Path Network, our mission is to protect our clients from cyber threats, no matter the size, the complexity, or how long they last. Recently, we demonstrated our capabilities when Interserver, a long-time customer, faced a significant DDoS attack. Here’s how we handled it.
Client Background: Interserver
Interserver has been a reliable web hosting provider since 1999. They offer various services, including shared hosting, cloud hosting, dedicated servers, and colocation. Known for their commitment to security and customer support, Interserver serves a wide range of clients, from freelancers to Fortune 500 companies.
Since 2021, Interserver has partnered with Path Network to enhance its DDoS protection capabilities. Our service protects their infrastructure and enables them to offer DDoS-protected "floating IPs" to their end customers. These floating IPs provide flexible and dynamic protection, ensuring uninterrupted service for their clients' servers. You can read more about it at https://www.interserver.net/tips/kb/floating-ip-w-path-net-dos-protection/
The DDoS Attack - multi vectored and spread across 5 hours
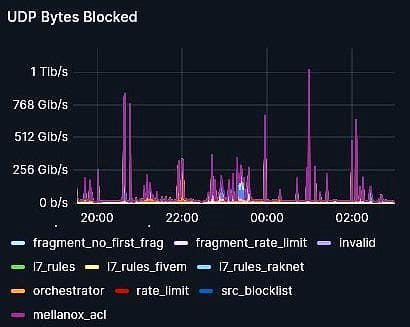
On July 31st, Interserver was targeted in a severe DDoS attack aimed at five specific IP addresses, all belonging to the same end-user. The attack was characterized by multiple spikes surpassing 500 Gbps, peaking at 1.2 Tbps and roughly 360 Mp/s (million packets per second) during five hours of intense activity.
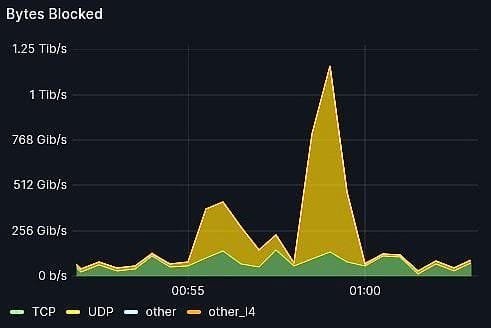
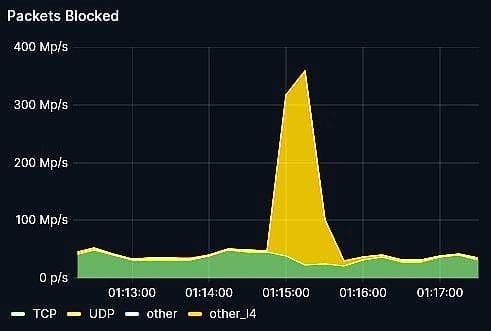
This attack began shortly after 8:00 PM PST and continued until around 1 PM, with the highest peak occurring towards the end of this period. The largest of these attacks combined UDP and GRE-based DDoS vectors, predominantly utilizing UDP. The attacker gave up shortly after noticing there was no impact, not even after using its resources at full capacity.
Path Network’s Mitigation Strategy
Our mitigation strategy is designed to handle even the most sophisticated DDoS attacks through a multi-layered approach:
- First Layer - Auto-Filtering: Our Orchestrator’s auto-filtering technology immediately identified and blocked the majority of the malicious traffic. This layer of protection is designed to handle large-scale volumetric attacks, such as those exceeding 1 Tbps.
- Second Layer - Stateful Firewall Rules: For any residual threats that bypassed the first layer, smaller but more complex DDoS vectors, the stateful firewall rules were activated. These rules were specifically added by the Interserver end-user in the customer dashboard, adapting the DDoS mitigation to the specifics of the applications he wanted to protect(whitelist, block or rate-limiting rules based on Traffic Protocols, Internet Ports, Source and Destination IPs, and so on).
- Third Layer - Custom-Built DDoS Filters: The final layer of defense involves the application of custom-built DDoS filters. These filters are selected from a predefined list available in the customer dashboard and are built based on the unique RFC documents for the applications they are meant to protect. This ensures that even the most complex and sophisticated attack vectors are effectively mitigated.
Outcomes and Impact
Thanks to our comprehensive mitigation strategy, the attack was fully neutralized without any disruption to Interserver or their end-users. The effectiveness of our approach was highlighted by the seamless continuity of Interserver’s services.
The end-user of Interserver did not feel any impact from the DDoS attack, a testament to the effectiveness of our protection. The Interserver team also did not notice any disruptions in their network, thanks to our successful mitigation efforts. The feedback was clear: "Overall, we did not have any issues or notice anything."
Lessons Learned and Best Practices
This incident serves as a reminder that DDoS attacks are not a matter of "if," but rather a matter of "when." Businesses must be prepared for the inevitability of such attacks and have the right partners and solutions in place. Our experience with Interserver demonstrates that effective DDoS mitigation requires a combination of volumetric attack handling and stateful, intelligent filtering to adapt to the specific needs of different applications.
At Path Network, we provide these capabilities and more, ensuring that our clients are always one step ahead of potential threats.
Is your network prepared for a DDoS attack? Contact Path Network today to learn how our DDoS mitigation solutions can protect your business. Ensure your network’s security with our proven strategies.
For more information, reach out to us at sales@path.net.
