How to drop 1 Tbps of DDoS traffic
On June 29th, 2021, a DDoS attack was launched against our network which peaked at roughly 1 Tbps. To date, this is the largest DDoS attack that we've successfully detected and mitigated.
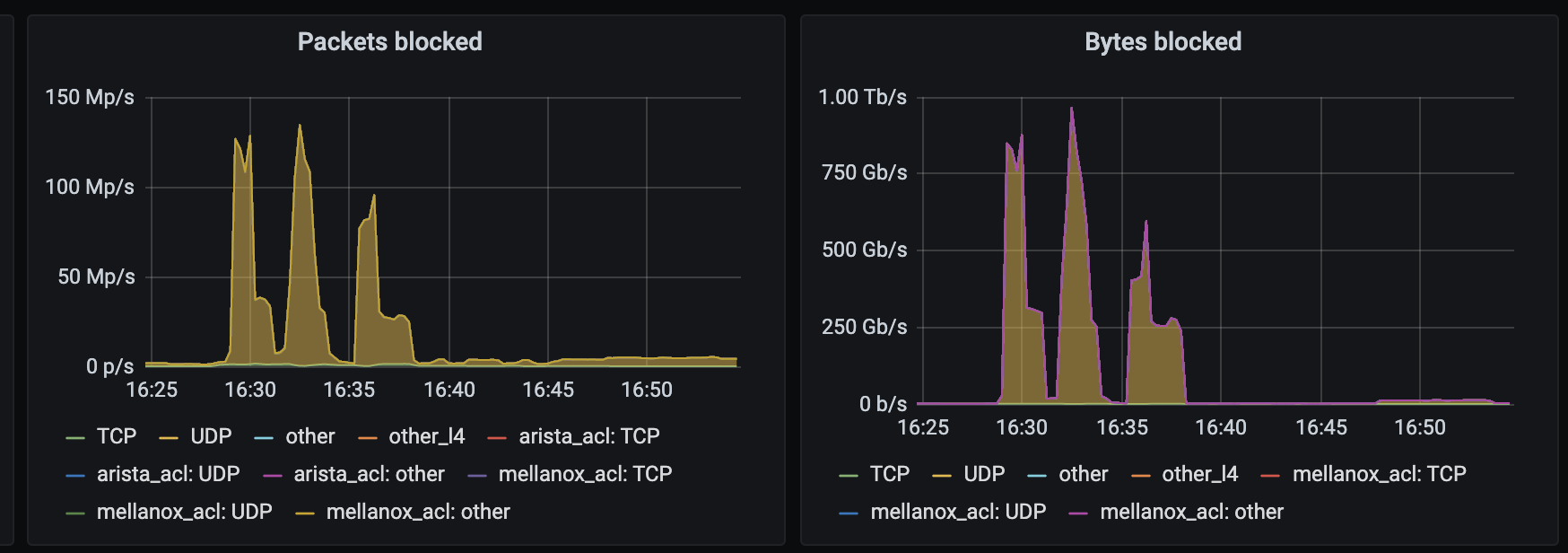
On June 29th, 2021, a DDoS attack was launched against our network which peaked at roughly 1 Tbps. To date, this is the largest DDoS attack that we've successfully detected and mitigated.
Analysis
While many attacks that we have seen in the past aim to disrupt certain services hosted by clients, this one specifically targeted our network. During the attack, we discovered various attempts to bounce requests off of legitimate servers on the Internet and towards us. We refer to this as a reflection attack, which has been described in a previous blog post. The services being used for reflection included common attack vectors such as STUN, DNS, NTP, and BitTorrent. It is very common for volumetric attacks to originate from UDP reflection/amplification. The chart below visualizes some of the most prevalent forms of DDoS attacks. Note that UDP fragmentation is typically the by-product of a UDP amplification attack. If the attacker can elicit a reply from the server being used for amplification which is larger than the MTU (typically 1500 bytes), then the datagram will be fragmented. This is frequently seen with DNS.
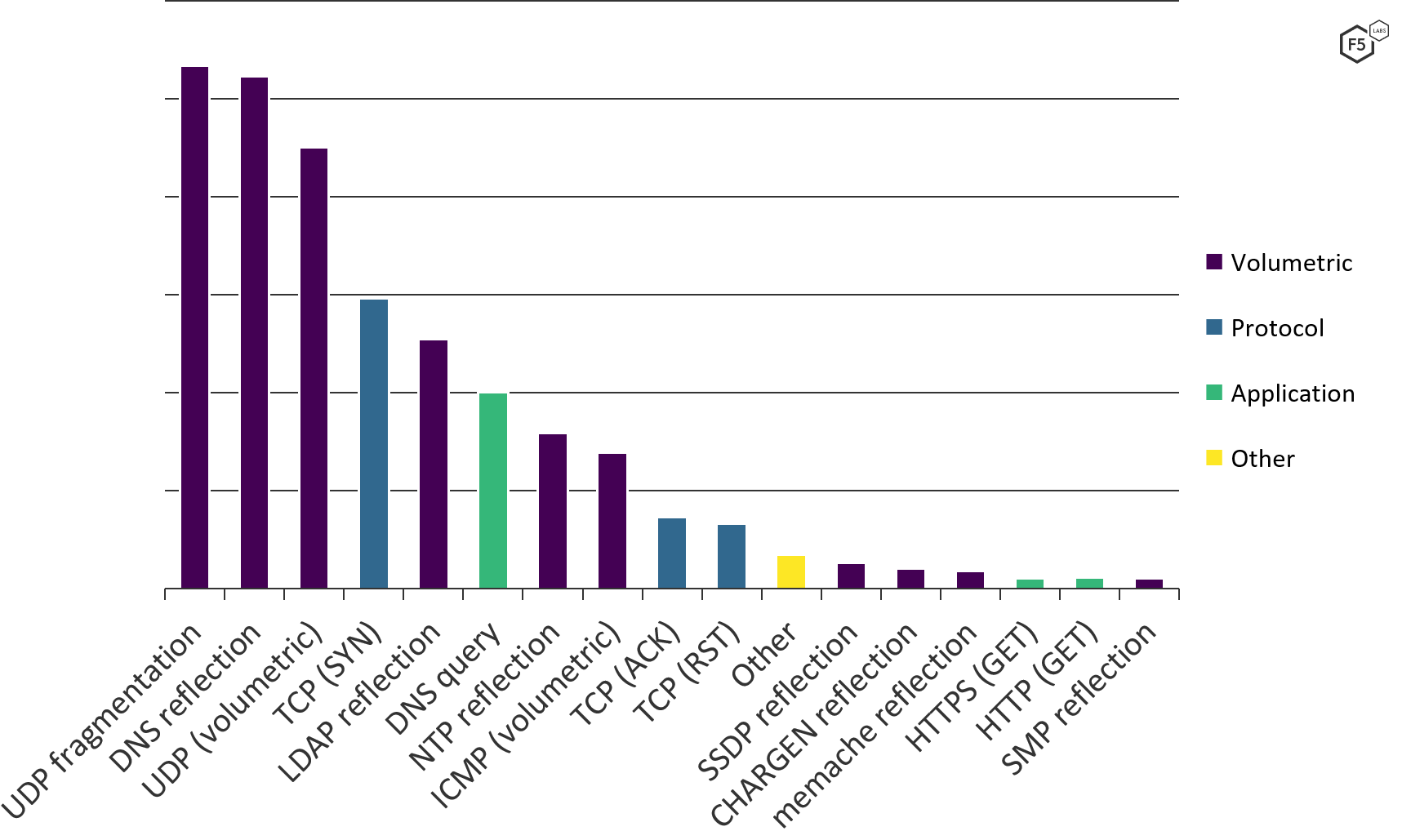
Some of the largest DDoS attacks can be attributed to UDP reflection or amplification. In February of 2018, Github was hit with a 1.3 Tbps attack which was carried out by exploiting memcached servers. Less than a week later, NetScout Arbor was targeted with a 1.7 Tbps DDoS attack that also used memcached. What Path observed was merely another indication that 2021 may follow the same attack trends.
Methodology
We were able to absorb this very large attack because of two primary reasons. Due to our constantly growing network, which currently has a capacity of over 6 Tbps, we are able to defend against attacks of any size. Furthermore, our state-of-the-art DDoS mitigation pipeline provides the necessary means to filter out malicious traffic at a blazing fast speed. Using Anycast technology, traffic destined towards an IP address on our network will be automatically routed to the nearest PoP. Each site is equipped with mitigation hardware running our cutting-edge eBPF/XDP stack. This allows us to filter out unwanted traffic at the edge of our network. Anycast also allows potentially malicious traffic to be more evenly distributed across the different PoPs, in turn reducing the chance of one site becoming overloaded. Immediately after the attack was launched, our sites kicked in and started scrubbing the traffic. This blend of both capacity and capability sets us ahead of competitors.
Outcome
During this event, our clients remained online and were not impacted. It was a great success to see our hard work in action. With the addition of new PoPs contributing to our global Anycasted network, Path has scaled very rapidly in a short amount of time. As Path's infrastructure continues to expand, our ability to protect users of the Internet from the growing threat of DDoS will only improve.
Lessons
This incident should serve as a reminder that DDoS attacks are still a prominent threat in the cyberspace. As we have seen, neither the frequency nor size of attacks appear to be going down. While efforts have certainly been made to limit these menacing network disruptions, such as Cloudflare deprecating the DNS ANY query type, denial-of-service attacks remain as a problem. As we collectively work to neutralize existing attack vectors, cybercriminals work to find replacements. With the seemingly endless expansion of the Internet, an increasing number of IoT devices makes for more systems that, when improperly configured or simply neglected, may add fuel to the fire of distributed attacks against networks. The effects of DDoS attacks can be catastrophic for businesses, which is why it is crucial to protect yourself with mitigation providers such as ourselves.
