MikroMassive: the Botnet Powering Multi-Terabit DDoS Attacks
“It ain’t a mosh pit if ain’t no injuries” – Travis Scott, STARGAZING
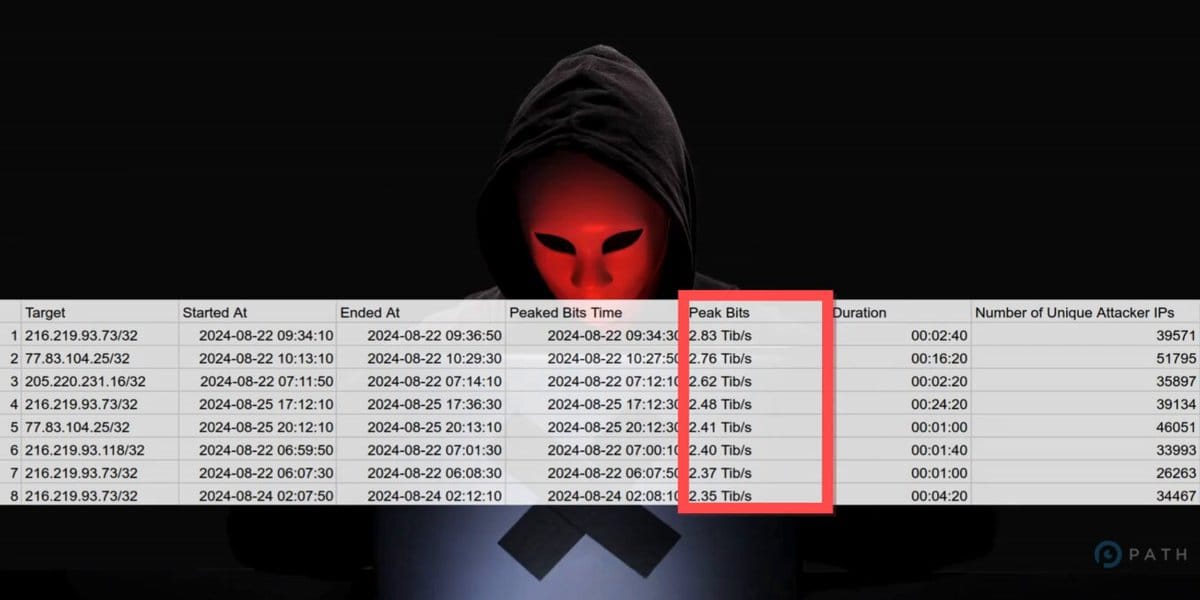
The following examines a collection of eight related attacks between August 22nd and 25th, 2024, which targeted three distinct Path-protected networks. These attacks, all with peak traffic rates over 2Tib/s, demonstrate a significant level of coordination and shared resources, suggesting they were launched from the same botnet. Because of the composition of this botnet, we’ve named it MikroMassive.
The Attacks
By analyzing the manner of attack, timing, target selection, and overlap in attacker IP addresses, we can draw a clear picture of how these attacks are interconnected.
Linking the DDoS Attacks: A Coordinated Campaign
All eight of these attacks were non-spoofed, UDP flood attacks targeting port 65535/UDP. This uniformity in the attack method suggests a possible connection between the incidents, as it shows a consistent strategy across the multiple attacks. While the shared manner of attack alone isn’t definitive proof of coordination, it does raise the likelihood that these attacks might be linked. To explore this possibility further, we conducted an in-depth analysis of the IP addresses involved in each attack.
By enumerating the IP addresses of all attacking hosts in each attack, we use the Jaccard Index to measure the significance of their overlap. The Jaccard Index is a measure of similarity between two sets, calculated as the size of their intersection divided by the size of their union. It ranges from 0 to 1, with higher values indicating greater similarity.
The attacks with the most overlap are the following:
- Attack 1 and Attack 2:
- Intersection: 35,980
- Jaccard Index: 0.64
- Analysis: These two attacks share a substantial number of IP addresses, indicating that they likely used the same or very similar botnets.
- Attack 3 and Attack 6:
- Intersection: 28,055
- Jaccard Index: 0.67
- Analysis: This high overlap in both absolute terms and relative size strongly suggests a close relationship between these two attacks.
- Attack 4 and Attack 5:
- Intersection: 32,661
- Jaccard Index: 0.62
- Analysis: These two attacks share a large number of IPs, indicating a significant reuse of resources between them.
Other Notable Overlaps:
- Attack 2 and Attack 3:
- Intersection: 29,580
- Jaccard Index: 0.50
- Analysis: While not as high as the above pairs, this overlap points to a likely connection between these attacks.
- Attack 1 and Attack 3:
- Intersection: 25,832
- Jaccard Index: 0.52
- Analysis: These attacks share a substantial portion of IP addresses, suggesting they may have been part of a coordinated effort.
- Attack 6 and Attack 7:
- Intersection: 20,065
- Jaccard Index: 0.49
- Analysis: Despite occurring on different targets, these attacks have a notable overlap in IP addresses, implying a link.
While we are not releasing the IP addresses of the targets to preserve the privacy of Path customers, we can say the following:
- Attack 1, Attack 4, Attack 7, and Attack 8 had the same target.
- Attack 2 and Attack 5 had the same target.
- Attack 3 had a unique target.
- Attack 6 had a unique target.
The eight attacks exhibit intricate relationships, strongly suggesting they are part of a coordinated campaign. All were UDP flood attacks targeting port 65535/UDP, indicating a consistent attack strategy across multiple incidents.
Attacks 1, 4, 7, and 8 all targeted the same IP address, indicating a persistent focus on a high-value target.
Furthermore, Attacks 1, 2, 3, and 6 are closely linked, sharing significant overlaps in attacker IPs, with intersections as high as 28,000 hosts, suggesting they likely utilized the same botnet or were orchestrated by the same group.
Attacks 4 and 5, which targeted different IPs, are also strongly connected, indicating a shared infrastructure or strategy.
Notably, Attack 3 is closely linked with Attack 6, and Attack 6 with Attack 7, creating a bridge that ties these attacks into the broader campaign.
Even Attack 8, while focusing on the same target as Attacks 1, 4, and 7, shows a significant overlap with Attacks 1, 2, and 3, with over 20,000 shared attacking hosts, reinforcing the likelihood that these distinct attacks are, in fact, part of a coordinated assault on multiple fronts.
The pattern of shared targets, overlapping attacker IPs, and a consistent UDP flood attack method targeting the same port across all eight attacks highlights a coordinated effort, indicating these incidents are not isolated but attacks from the same botnet.
Geographic Distribution of Attacking Hosts
Our analysis of the DDoS attacks identified a total of 90,888 unique hosts participating across all incidents. The geographic distribution of these botnet participants provides insights into the global nature and potential origins of the attacks.
Russia has the most attackers with 14,353 hosts, followed closely by Vietnam with 11,622 hosts. These two countries alone account for over 28% of the total botnet participants, suggesting that they are significant hubs for the infrastructure used in these attacks. The high concentration of botnet participants in Russia and Vietnam could indicate a combination of factors, including the prevalence of vulnerable devices and potentially less stringent cybersecurity measures.
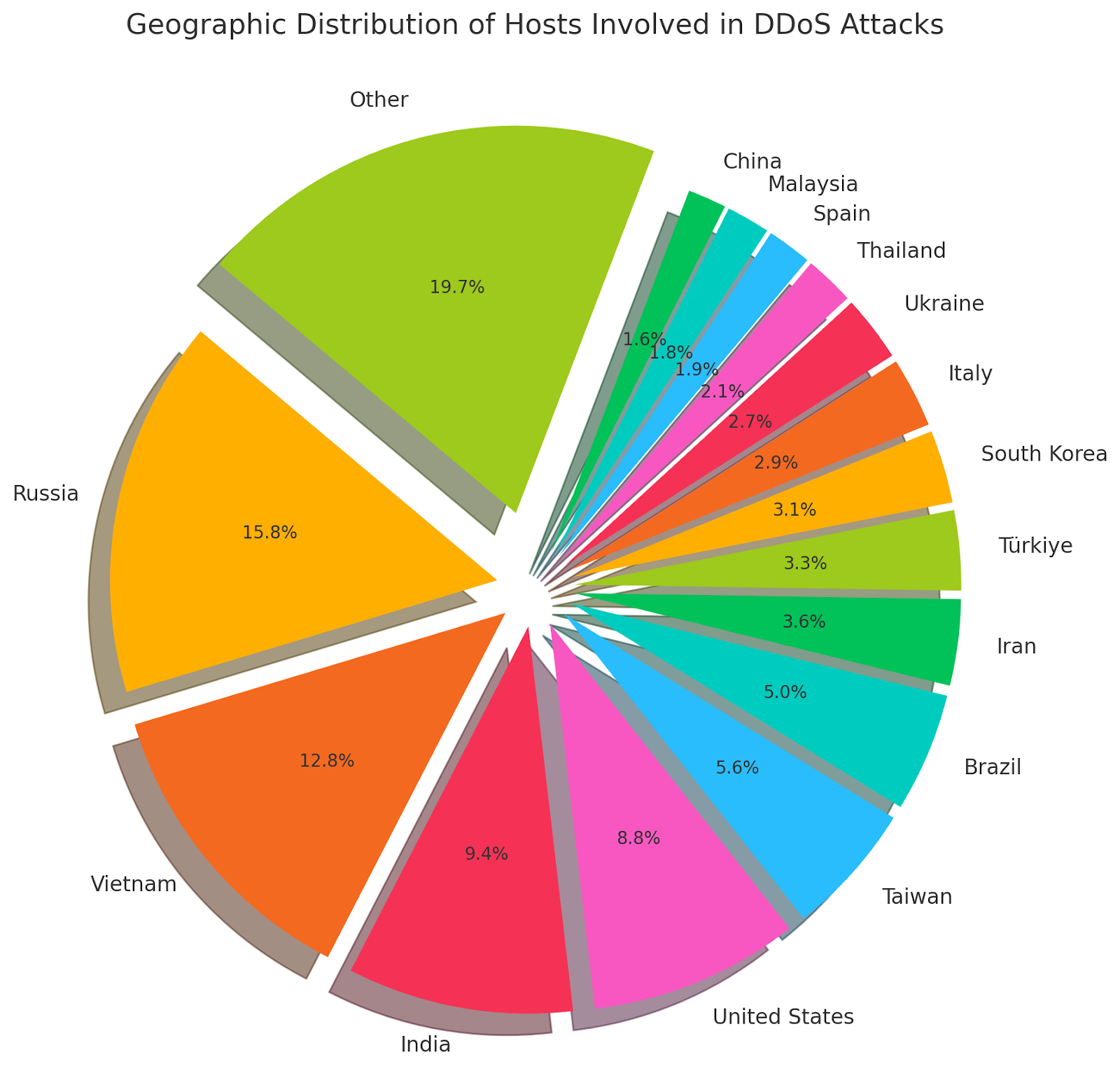
India and the United States also feature prominently, with 8,584 and 7,978 hosts respectively. The presence of a large number of hosts in these countries underscores the global footprint of the botnet, highlighting that while some regions may be more heavily targeted for recruitment, the impact of these attacks is truly global.
Taiwan and Brazil contribute 5,073 and 4,530 hosts respectively, and countries like Iran (3,276), Türkiye (3,036), and South Korea (2,779) also show significant participation, indicating that the botnet's reach extends deep into both developed and developing nations.
This geographic spread suggests several important considerations:
- Distributed Botnet Infrastructure: The diversity in geographic origin points to a highly distributed botnet, utilizing compromised devices or proxies from various regions to enhance resilience against takedown efforts and to complicate mitigation strategies.
- Regional Variations in Vulnerability: The significant numbers of hosts from Russia, Vietnam, India, and other countries may reflect regional differences in cybersecurity practices or the availability of vulnerable devices that can be easily compromised and conscripted into botnets.
- Strategic Host Selection: The selection of hosts from a wide array of countries might be a deliberate strategy to avoid easy detection and to spread the attack load, making it more challenging for defenders to block traffic based on geographic origin.
This global distribution of botnet participants underscores the challenge of modern cybersecurity, where attacks are not confined by borders and can leverage vulnerable devices worldwide.
Anatomy of the Botnet: The Devices Behind the DDoS
The botnet responsible for the DDoS attacks observed in August 2024 is composed of a diverse array of compromised devices and systems, each playing a role in amplifying the scale and persistence of the attacks. By analyzing the characteristics of these hosts, we can better understand the infrastructure leveraged by the attackers.
We performed an analysis on a sample of 23,000 hosts from the 90,888 unique IPs we identified as participating in the DDoS attacks. Using the Nmap host identification feature, we scanned this subset to gather information about the types of devices involved. Nmap's host identification allowed us to infer the operating system and, in some cases, the specific device type, which formed the basis of our analysis.
It is important, however, to acknowledge the limitations of this approach. First, we scanned only a fraction of the total hosts, so the results are based on this sample, which may not fully represent the entire botnet. Additionally, Nmap's scans are more likely to identify the routers or other network-facing devices rather than the machines behind them, potentially obscuring the true origin of some traffic. Network configurations like firewalls, proxies, or NAT (Network Address Translation) could further complicate accurate identification. It’s also worth noting that Nmap’s OS identification feature has inherent limitations—it relies on network fingerprints, which can sometimes lead to inaccuracies. It’s possible for this to result in misclassification of devices, further complicating the overall picture.
That being said, despite these challenges, we believe these findings offer valuable insights into the potential composition of the botnet. The prominence of certain device types, such as routers and smart systems, suggests that the attackers are taking advantage of widely deployed, often poorly secured devices, which are highly effective at amplifying attacks of this scale.
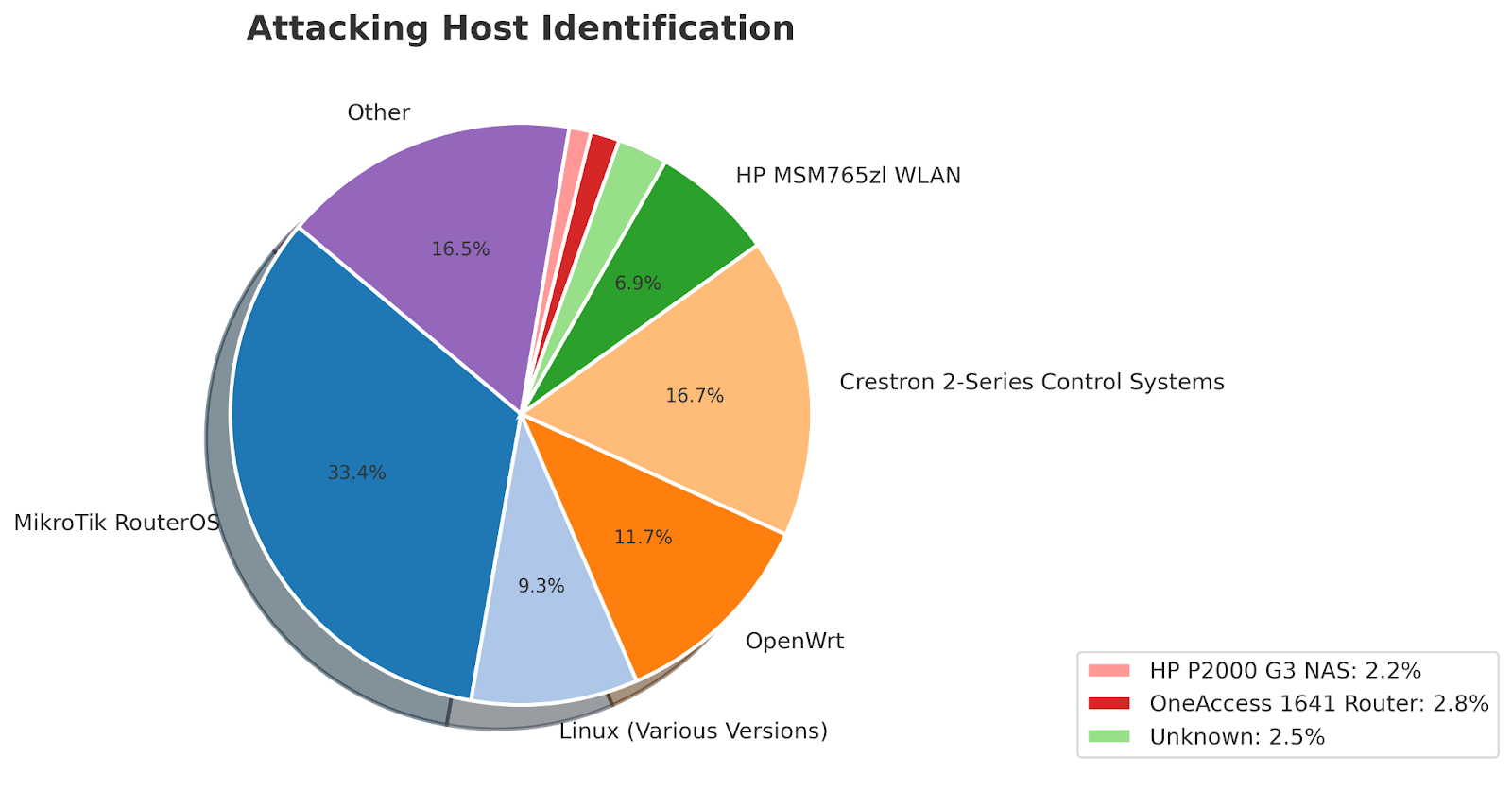
1. MikroTik RouterOS Devices (33.4%)The largest proportion of the botnet, over 33%, consists of MikroTik RouterOS devices. These routers, often used in networking infrastructure, are known for their powerful configurations but have also been frequent targets of exploitation due to vulnerabilities in older firmware versions. The widespread use of MikroTik devices in various industries makes them prime candidates for recruitment into botnets, especially when left unpatched.
2. Crestron 2-Series Control Systems (16.7%)A significant portion of the botnet—16.7%—is made up of compromised Crestron 2-Series Control Systems. These devices, commonly used in high-end home and commercial automation, are designed to control a wide range of systems including AV, lighting, and environmental controls. The 2-Series line was first introduced in the early 2000s and has been succeeded by newer models, making these devices relatively old and more vulnerable to exploitation.
Despite their age, 2-Series systems are still widely deployed, particularly in environments where they have not been updated or replaced. Like many legacy devices, these systems can suffer from outdated firmware and lack modern security protections. As a result, many of these devices have likely been co-opted into the botnet due to poor security configurations or being left exposed on public networks without proper protection.
3. OpenWrt Routers (11.7%)Around 16% of the botnet is composed of devices running OpenWrt, an open-source Linux-based operating system typically used in embedded devices such as home routers. Notably, a significant portion of these devices — 94.6% — were identified as running OpenWrt Kamikaze (version 7.09). According to the OpenWRT wikipedia page this version was released 2007-06-02. This suggests that attackers are primarily exploiting older, more widely-deployed firmware versions, which are likely to have unpatched vulnerabilities which make these devices easier to compromise.
4. Hewlett Packard MSM765 ZL WLAN Controllers (6.9%)The Hewlett Packard MSM765 ZL WLAN Controller was released in 2009 as part of HP's ProCurve Networking line, designed for enterprise environments to manage and secure wireless access points. This controller is no longer sold and is considered an older device, making it more vulnerable to exploitation, especially when not updated with the latest firmware. Over the years, several Remote Code Execution (RCE) vulnerabilities have been reported in this product.
Given that the HP MSM765 ZL often functions as a gateway device, it is possible that some of the attack traffic we observed came from compromised devices within networks behind these controllers. Attackers could be leveraging the controller’s position in the network to amplify their attacks, making it difficult to identify the true origin of the traffic. This type of problem adds a layer of complexity in attempting to attribute DDoS attacks.
While much of the botnet is composed of well-known devices like routers and control systems, there remains a significant portion—approximately 16.5%—that falls under the “Other” category, these included HP Photosmart printers, Cisco VoIP devices, Windows Operating Systems, Netgear and Fortinet network devices, and even some Geovision EBD4700 CCTV cameras (based on Linux). A large portion of the botnet, 9.3%, was identified as devices running different versions of Linux, based on Nmap's classification. These devices often had secondary identifications, indicating that Nmap recognized the base Linux system but suggested an embedded system or router as a more specific match. The presence of such diverse devices, along with 2.5% of devices that remain unidentified, illustrates how attackers are capable of incorporating a broad spectrum of hardware into their botnet operations, leveraging both enterprise-grade infrastructure and consumer electronics. Attackers are no longer restricted to any single type of device; instead, they leverage the weaknesses across a wide range of technologies to conduct large-scale, coordinated attacks.
Conclusion: Limitations and Future Work
In this post, we link 8 large DDoS attacks occurring over 4 days to a single botnet of over 90,000 unique hosts. We dubbed this botnet 'MikroMassive' because over a third of its devices appear to be MikroTik routers, making them a key driving force behind the high-volume DDoS traffic. Other DDoS researchers observed large attacks during the same time period, and we wonder if they are from the same botnet.
While these findings provide some insight into the MikroMassive botnet, there is still much work to be done. We have not yet identified the specific malware controlling this botnet, and the command and control infrastructure remains unknown. Understanding how attackers are managing and coordinating this botnet would provide crucial intelligence for disrupting its operations. Additionally, while our scan of 23,000 hosts offers a strong representative view of the botnet, a more comprehensive analysis of the full 90,888 hosts could yield even deeper insights.
Large-scale DDoS attacks have unfortunately become a persistent feature of the modern threat landscape. At Path, we routinely mitigate attacks exceeding 1Tb/s on a daily basis. In fact, while we were researching the MikroMassive botnet and compiling these findings, Path has continued successfully defended against DDoS incidents, some surpassing 2Tb/s. Although roughly half of these attacks involved spoofed traffic—making it harder to trace the true source, as we’ve discussed in this post—it’s clear that a significant portion of the ongoing attacks share characteristics with those from the MikroMassive botnet. This suggests that this botnet remains active, and we are likely to encounter its impact for some time to come.
Here at Path, we provide our clients with a multi-layer mitigation architecture capable of withstanding the largest DDoS attacks on the planet. Our adaptive filtering technology provides best-in-class defense. Against these recent attacks, this feature has demonstrated outstanding results in blocking UDP-based DDoS attacks. For further information, please contact sales@path.net.
Twitter: https://twitter.com/path_network
